

With AI-powered threat detection, cloud security, and compliance-driven frameworks, we proactively safeguard businesses from cyberattacks, ensuring data privacy and business continuity.
At Netovate, our VAPT services help organizations uncover hidden weaknesses before attackers do. We conduct thorough assessments and simulate real-world cyberattacks to evaluate the security posture of your applications, networks, and infrastructure.
Comprehensive Vulnerability Scanning – Identify weaknesses across systems, applications, and endpoints.
Manual & Automated Penetration Testing – Simulate real-world attack scenarios to test resilience.
Risk-Based Reporting – Prioritized recommendations to fix critical issues fast.
Compliance-Ready Testing – Support for GDPR, ISO 27001, HIPAA, PCI-DSS, and more.
Remediation Support & Re-Testing – Guidance to patch vulnerabilities and validate fixes.


Threat & Vulnerability Assessments – Identifying security gaps in systems and applications.
Security Posture Evaluation – Measuring how well your business can withstand cyber threats.
Risk Mitigation Strategies – Recommending security enhancements to fortify your defenses.
Regulatory Audits – Ensuring compliance with industry standards like GDPR, HIPAA, and ISO 27001.
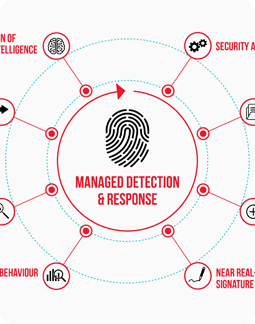
With the rise of ransomware, phishing attacks, and data breaches, organizations must be prepared to detect and respond to security incidents swiftly. Netovate’s AI-driven cybersecurity solutions provide real-time monitoring, rapid incident response, and post-attack analysis to minimize damage and ensure business continuity.
24/7 Security Monitoring – Continuous surveillance to detect anomalies.
Advanced Threat Intelligence – AI-powered analytics to predict cyber threats.
Incident Response Planning – Immediate containment and mitigation strategies.
Forensic Investigation & Reporting – Root cause analysis and security improvements.

As businesses increasingly move to the cloud, ensuring secure data access, encrypted communication, and firewall protection is crucial. Netovate provides next-gen network security solutions to safeguard IT environments from unauthorized access, malware, and cyber intrusions.
Firewall & Intrusion Prevention Systems (IPS) – Blocking external cyber threats.
Cloud Security Frameworks (AWS, Azure, Google Cloud) – Protecting cloud-hosted applications and data.
Zero Trust Security Model Implementation – Ensuring only authorized users can access critical data.
Secure VPN & Remote Access Solutions – Enabling safe connectivity for remote teams.

Unauthorized access is one of the biggest security risks organizations face today. Netovate’s IAM solutions ensure only verified users and devices gain access to critical business resources, helping prevent insider threats and unauthorized data breaches.
Multi-Factor Authentication (MFA) – Adding extra layers of security beyond passwords.
Role-Based Access Control (RBAC) – Restricting access based on user roles.
Single Sign-On (SSO) Integration – Simplifying secure access for employees.
Privileged Access Management (PAM) – Securing administrative and high-risk accounts.

Many industries require businesses to follow strict cybersecurity regulations to protect sensitive data and prevent financial or legal penalties. Netovate ensures your organization remains compliant with global and industry-specific standards.
GDPR Compliance – Ensuring the privacy of user data under European regulations.
HIPAA Compliance – Protecting healthcare data from unauthorized access.
ISO 27001 Security Standards – Implementing a globally recognized information security framework.
NIST & SOC 2 Implementation – Enhancing cybersecurity maturity for service providers.
Prevent data breaches and cyberattacks
Meet security compliance requirements
Build trust with customers and stakeholders
Strengthen your organization's overall cyber resilience
24/7 Cybersecurity Support – Ensuring round-the-clock protection for your business.
Secure your business with Netovate. Contact us today!



